No single factor has been more responsible for the proliferation of working remotely than the ability to gain secure access to office networks and cloud-based applications from outside of the office. In an earlier blog, I wrote about the advantages of Virtual Private Networks for the home worker to gain access to necessary corporate systems. I have also written about the benefits of accessing cloud-based tools like Asana and Slack to improve nearly every aspect of working remotely. Yet all these applications and services have one thing in common…user authentication via logging in. It is the Achilles heel of all things that require managed access. No system can be useful unless the application is certain that it is really YOU logging in! You need to be authenticated by nearly every useful tool on your phone and laptop.
And, in the realm of user login authentication, passwords are still king. Passwords have been around since before software was distributed on floppy disks and CDs. A password was required to install operating systems, load programs onto your laptop, and more recently, to load apps on your smartphone.
3 Types of Authentication Factors
Of course, other forms of user authentication exist. Generally speaking, there are three types of authentication factors. Passwords fall into the first type of authentication, categorized as Something You Know.
Something You Know
This type of authentication includes the following:
- Password
- Personal Identification Number (PIN) or pattern lock
- Combination
Something You Have
The second type of authentication is best summarized as Something You Have, which might include one of the following:
- Smartphone
- USB drive
- Smart card or token
- Key
Using two (or more) of these factors, known as multi-factor authentication, is a growing trend. I currently log in to several systems by first providing a user name and password and then accepting the connection via a pop-up on my cell phone, sent by the authenticating system.
Something You Are
The third, and final, type of authentication is grouped as Something You Are, also known as biometrics, and include the following:
- Fingerprint
- Facial recognition
- Voice verification
A smartphone uses either a password (passcode or pattern), fingerprint, or facial recognition to gain access. The biometrics provide quick access to your device. However, if you want to upgrade the phone’s operating system, you need to know the passcode!
So, even with the advent of new technologies, the password reigns supreme. And EACH device and application requires a password. Most systems have requirements for various aspects of passwords like:
- Minimum number of characters
- Number of character sets (a-z, A-Z, 0-9, !@#$%^&*()_+-=) that must be included
- Frequency of change (password age)
- Numerous other restrictions, like location of special characters in the string, etc.
5 Password Tips
Given all this, here is my first tip regarding passwords:
Tip #1: Password length trumps complexity. A longer password is more secure, even with just the minimum complexity.
For example, if you were to use a variation of today’s date - September 12, 2019 - as your password, and each met the minimum complexity of one lowercase letter, one uppercase letter, one number, and one special character, here is the time it would take a single computer to crack your password, according to How Secure Is My Password (howsecureismypassword.net):
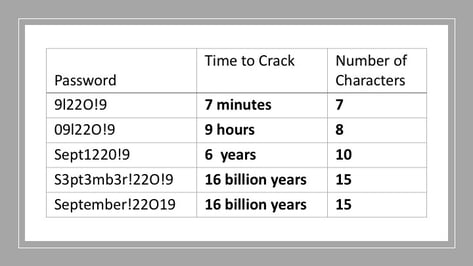
The last two examples show the point. Adding extra special characters or uppercase letters does not strengthen the password. The last example includes only one uppercase letter and one special character. It is simpler to remember and is just as secure as any other 15-character password that meets the requirements. So, use a pneumonic like a date as your password, but remember to implement it with many characters. A phrase like TodayIsSeptember122019! works even better! This password would take 19 septillion years to crack!
But, as we all know, the difficult part of accessing systems is not creating a secure password. It is remembering them all! By my last count, I have over 100 user IDs and passwords to remember on my laptop and smartphone. So, this leads to my second password tip.
Tip #2: Do not use the same password on different systems!
The obvious flaw with sharing passwords across systems is that if your password gets hacked on one system, your other accounts that use the same password are suddenly vulnerable. So, every application and system you access needs a unique password and most need to be changed on a regular basis. How is anyone expected to remember them all? The answer is my third password tip.
Tip #3: Use a password manager like LastPass to store all your passwords in one location online.
This free web service stores all your passwords in an encrypted format. The included browser plugin collects your login information as you log into each system and stores them as encrypted data in the cloud. Then, the next time you log into that system from your browser, LastPass automatically retrieves and provides your credentials. The reality is that, with a password manager, you don’t even need to actually know or remember your individual passwords for each system. You can even accept one of those cryptic site-recommended passwords because LastPass remembers it for you. And this leads to my fourth password tip.
Tip #4: Do not ever forget your password manager master password!
Even the good folks at LastPass cannot help you recover your master LastPass password if you forget it! As a security feature, your password is not stored anywhere on their system in plain text. Even if their servers get hacked, the bad guys will only see encrypted strings representing your various system passwords.
Biometrics and the use of dual-factor authentication definitely have improved the world of user authentication. However, passwords are here to stay. So, do yourself a favor, and take advantage of a password management system and ease the password burden in your life. But please remember my fifth and final tip.
Tip #5: DON’T EVER FORGET YOUR PASSWORD MANAGER MASTER PASSWORD!




.jpg)
.jpg)
.jpg)
.jpg)
-1.jpg)
.jpg)


.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
-1.jpg)

